Setting up a Virtual Private Cloud (VPC) is essential for securing your IoT infrastructure, and this RemoteIoT VPC tutorial aims to provide a step-by-step guide to help you get started. In today’s interconnected world, where devices communicate and share data seamlessly, the importance of a secure and scalable network cannot be overstated. This RemoteIoT VPC tutorial will take you through the process of creating a VPC, configuring subnets, and setting up security groups to ensure your IoT ecosystem operates efficiently and securely.
Whether you're a seasoned IT professional or just starting your journey into the realm of IoT, this RemoteIoT VPC tutorial will equip you with the knowledge and tools necessary to build a robust network architecture. By the end of this tutorial, you’ll have a clear understanding of how to leverage AWS VPC services to manage your IoT devices effectively. With the rise in cyber threats and the increasing reliance on IoT technology, securing your network has become more critical than ever.
This RemoteIoT VPC tutorial is designed to be beginner-friendly, ensuring that even those with limited technical expertise can follow along effortlessly. We’ll cover everything from basic concepts to advanced configurations, so you can tailor the setup to meet your specific needs. Let’s dive in and explore how to create a secure, scalable, and efficient IoT infrastructure using AWS VPC.
Read also:Did The Rock Die Today 2025 Debunking Myths And Celebrating A Legend
Table of Contents
- What is VPC?
- RemoteIoT VPC Tutorial Overview
- Why is VPC Important for IoT?
- How to Set Up VPC for RemoteIoT?
- What Are the Security Best Practices?
- Common Mistakes to Avoid
- RemoteIoT VPC Tutorial: Advanced Configurations
- How Can You Optimize VPC for IoT?
What is VPC?
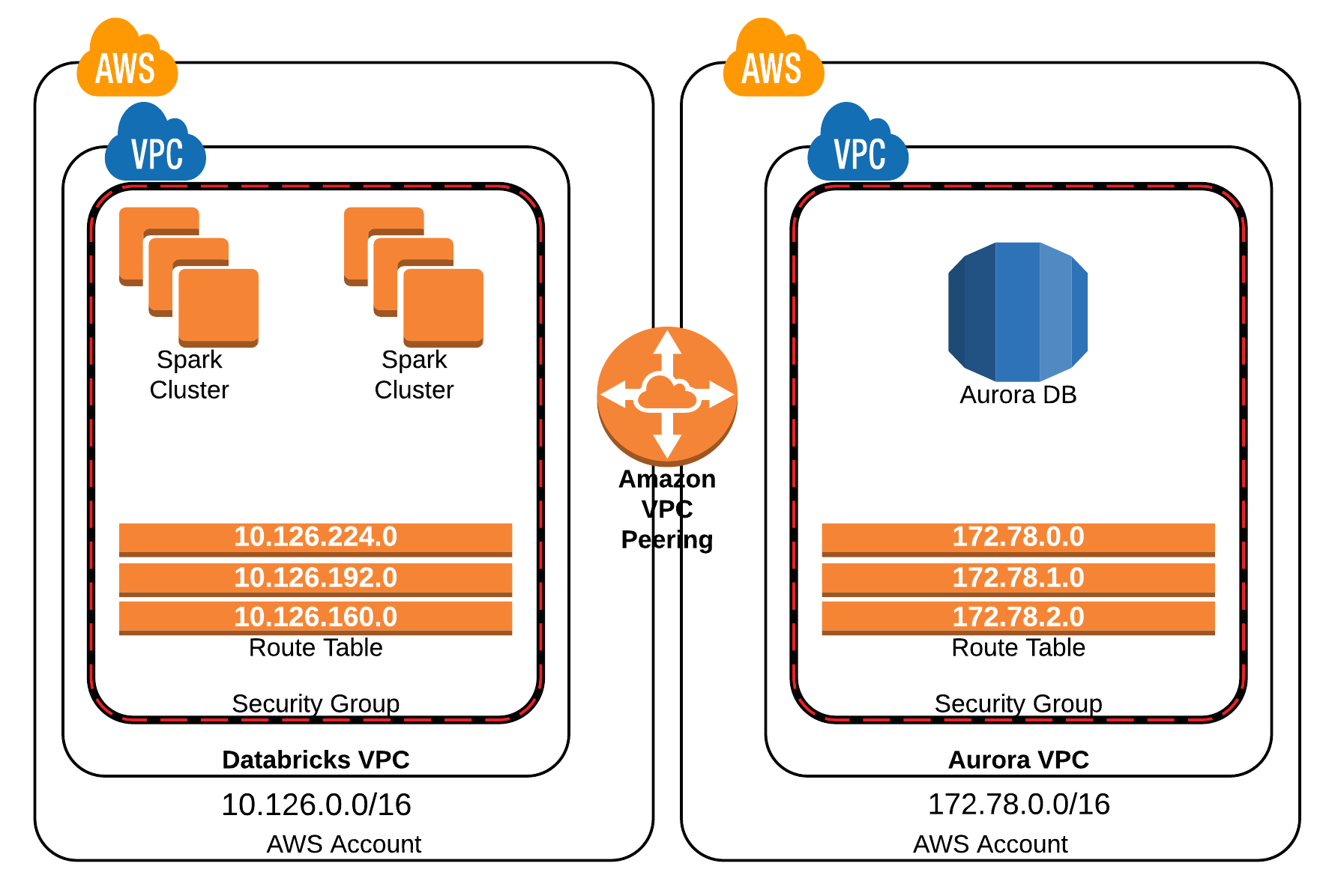
A Virtual Private Cloud (VPC) is a logically isolated section of the Amazon Web Services (AWS) cloud where you can launch AWS resources in a virtual network that you define. This virtual network closely resembles a traditional data center, allowing you to have complete control over your network configuration. With a VPC, you can choose your own IP address range, create subnets, configure route tables, and set up network gateways.
For IoT applications, a VPC provides a secure environment for your devices to communicate and exchange data. It ensures that your IoT infrastructure is protected from unauthorized access and potential cyber threats. By leveraging AWS VPC services, you can create a network architecture that is both scalable and flexible, accommodating the growing demands of your IoT ecosystem.
VPCs offer several advantages, including enhanced security through network isolation, flexible network configuration options, and the ability to integrate with on-premises networks. These features make VPC an ideal choice for securing your IoT infrastructure, ensuring that your devices operate efficiently and securely.
RemoteIoT VPC Tutorial Overview
This RemoteIoT VPC tutorial will walk you through the process of setting up a VPC for your IoT devices. We’ll start by covering the basics of VPC and then delve into the specifics of configuring subnets, setting up security groups, and managing access controls. By the end of this tutorial, you’ll have a comprehensive understanding of how to create a secure and scalable IoT network using AWS VPC services.
Some of the key topics we’ll cover include:
- Creating a VPC and configuring subnets
- Setting up security groups and access controls
- Configuring route tables and network gateways
- Monitoring and troubleshooting your VPC
Each step will be explained in detail, ensuring that you can follow along with ease, regardless of your technical background. Let’s get started!
Read also:Eagles Austin Mn Your Ultimate Guide To Discovering The Heart Of Minnesota
Why is VPC Important for IoT?
In the world of IoT, where devices are constantly communicating and sharing data, security is paramount. A VPC provides a secure environment for your IoT devices, protecting them from unauthorized access and potential cyber threats. By isolating your IoT infrastructure in a VPC, you can ensure that only authorized devices and users can access your network.
VPC also offers flexibility and scalability, allowing you to easily expand your IoT ecosystem as needed. With the ability to create multiple subnets and configure network settings to meet your specific requirements, a VPC ensures that your IoT infrastructure can grow and adapt to changing demands. Additionally, VPC integrates seamlessly with other AWS services, providing a comprehensive solution for managing your IoT devices.
By leveraging VPC for your IoT applications, you can create a secure, scalable, and efficient network architecture that meets the needs of your organization. This RemoteIoT VPC tutorial will guide you through the process of setting up a VPC for your IoT devices, ensuring that your network is both secure and optimized for performance.
How to Set Up VPC for RemoteIoT?
Setting up a VPC for your RemoteIoT devices involves several steps, each of which is crucial for ensuring the security and efficiency of your IoT infrastructure. In this section, we’ll walk you through the process of creating a VPC, configuring subnets, and setting up security groups.
Step 1: Create a VPC
To begin, log in to your AWS Management Console and navigate to the VPC Dashboard. From there, select "Start VPC Wizard" and choose the VPC configuration that best suits your needs. For most IoT applications, a VPC with public and private subnets is recommended, as it provides a balance of security and accessibility.
Key Considerations:
- Choose an IP address range that doesn’t overlap with your existing networks
- Decide on the number and size of subnets you’ll need
- Configure DNS settings to enable name resolution within your VPC
Once you’ve made your selections, review your settings and create your VPC. This will serve as the foundation for your IoT network, providing a secure and isolated environment for your devices.
Step 2: Configure Subnets
After creating your VPC, the next step is to configure subnets. Subnets allow you to divide your VPC into smaller networks, each with its own IP address range. This is particularly useful for IoT applications, as it enables you to group devices based on their function or location.
When configuring subnets, consider the following:
- Public subnets for devices that need internet access
- Private subnets for devices that should remain isolated from the internet
- Azure availability zones to ensure high availability and fault tolerance
By carefully planning your subnet configuration, you can optimize the performance and security of your IoT network.
What Are the Security Best Practices?
When setting up a VPC for your RemoteIoT devices, security should be a top priority. Implementing best practices can help protect your IoT infrastructure from unauthorized access and potential cyber threats. Here are some key security measures to consider:
Implement Security Groups
Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic at the instance level. By defining rules that specify which traffic is allowed, you can ensure that only authorized devices and users can access your IoT network.
Some best practices for security groups include:
- Limiting inbound traffic to only the necessary ports and IP addresses
- Using security groups to control access between instances within your VPC
- Regularly reviewing and updating your security group rules to reflect changes in your network
Use Network Access Control Lists (ACLs)
Network ACLs provide an additional layer of security by controlling traffic at the subnet level. Unlike security groups, which operate at the instance level, network ACLs can be used to enforce rules across multiple instances within a subnet.
Best practices for network ACLs include:
- Defining explicit allow and deny rules for inbound and outbound traffic
- Monitoring and logging ACL activity to detect and respond to potential threats
- Regularly reviewing and updating your ACL rules to ensure they remain effective
By implementing these security best practices, you can create a secure and resilient IoT network that protects your devices and data from potential threats.
Common Mistakes to Avoid
While setting up a VPC for your RemoteIoT devices, it’s important to avoid common mistakes that could compromise the security and efficiency of your IoT infrastructure. Here are some pitfalls to watch out for:
1. Overlooking Security Group Rules
One common mistake is failing to properly configure security group rules. This can result in unauthorized access to your IoT network or unnecessary restrictions that hinder device communication. To avoid this, carefully review your security group rules and ensure they align with your security requirements.
2. Neglecting Network ACLs
Another common oversight is neglecting to use network ACLs to control traffic at the subnet level. By relying solely on security groups, you may miss opportunities to enhance the security of your IoT network. Be sure to implement network ACLs as part of your overall security strategy.
Avoiding these common mistakes can help ensure that your IoT infrastructure is both secure and efficient, providing a reliable foundation for your devices to operate.
RemoteIoT VPC Tutorial: Advanced Configurations
Once you’ve set up the basics of your VPC, you can explore advanced configurations to further enhance the security and performance of your IoT network. In this section, we’ll cover some advanced topics, including route tables, network gateways, and monitoring tools.
Route Tables
Route tables determine how traffic is routed within your VPC. By configuring route tables, you can control the flow of traffic between subnets and ensure that your devices communicate efficiently. For example, you might set up a route table that directs traffic from private subnets to a NAT gateway, enabling devices in those subnets to access the internet without exposing them directly.
Network Gateways
Network gateways provide connectivity between your VPC and other networks, such as the internet or your on-premises data center. By configuring network gateways, you can ensure that your IoT devices have the necessary access to external resources while maintaining a secure network environment.
Some common types of network gateways include:
- Internet gateways for accessing the internet
- NAT gateways for enabling outbound internet access from private subnets
- Virtual private gateways for establishing a secure connection to your on-premises network
How Can You Optimize VPC for IoT?
Optimizing your VPC for IoT involves fine-tuning your network configuration to meet the specific needs of your IoT devices. By making adjustments to your VPC settings, you can improve the performance and efficiency of your IoT network, ensuring that your devices operate smoothly and securely.
Monitor and Analyze Network Traffic
Monitoring your network traffic is essential for identifying potential issues and optimizing your VPC configuration. By using tools like AWS CloudWatch and VPC Flow Logs, you can gain insights into your network activity and make data-driven decisions to improve performance.
Regularly Review and Update Your Configuration
As your IoT ecosystem grows and evolves, it’s important to regularly review and update your VPC configuration to ensure it continues to meet your needs. This may involve adjusting subnet settings, updating security group rules, or modifying route tables to accommodate changes in your network.
By following these optimization strategies, you can create a VPC that is tailored to the unique requirements of your IoT devices, providing a secure and efficient environment for them to operate.
Frequently Asked Questions
1. What is the difference between a security group and a network ACL?
A security group acts as a virtual firewall for your instances, controlling traffic at the instance level, while a network ACL controls traffic at the subnet level. Security groups are stateful, meaning they automatically allow return traffic, whereas network ACLs are stateless and require explicit rules for both inbound and outbound traffic.
2. How can I ensure my VPC is secure?