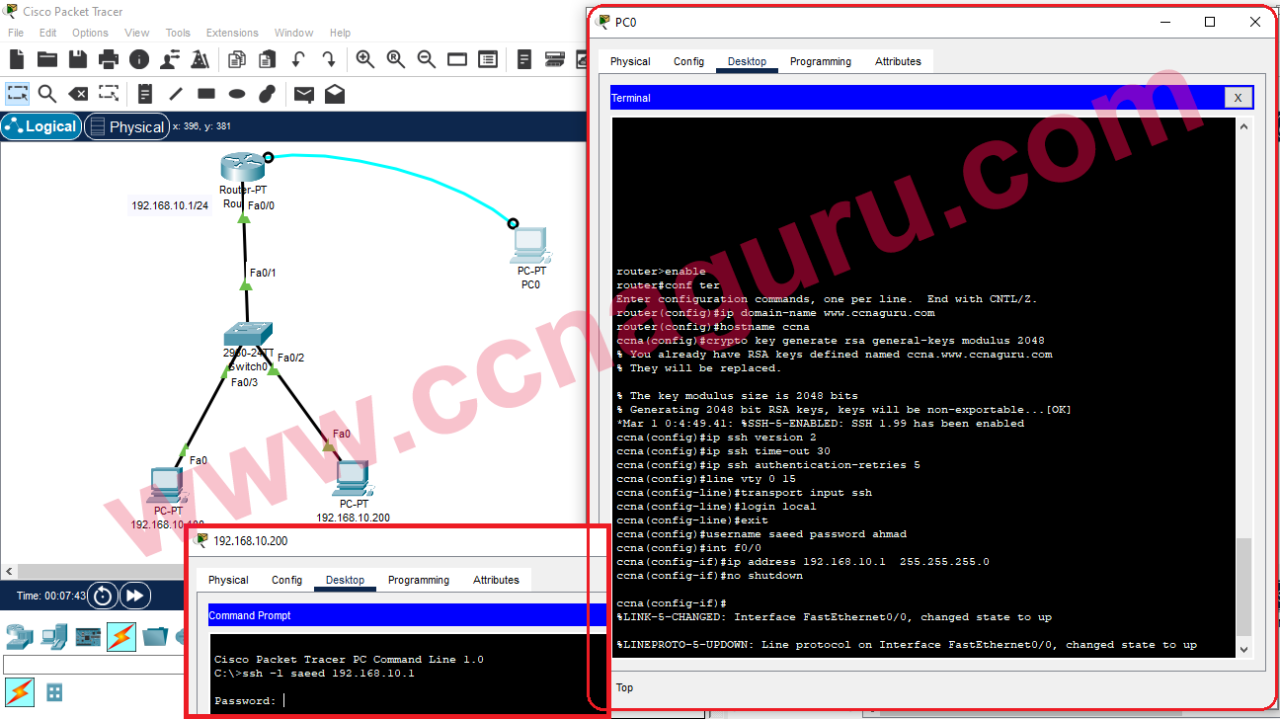
Securing remote SSH access is an essential practice for anyone managing servers or working in IT. As cyber threats continue to evolve, ensuring that your Secure Shell (SSH) connections are protected has never been more critical. Imagine leaving your front door unlocked in a neighborhood with high crime rates—it’s a recipe for disaster. Similarly, unsecured SSH access can expose your systems to unauthorized access, data breaches, and malicious attacks. In today’s digital landscape, where remote work and cloud computing dominate, understanding how to secure SSH connections is not just beneficial—it’s vital.
SSH, or Secure Shell, serves as a secure channel over an unsecured network, enabling encrypted communication between two systems. However, its security depends on how well it’s configured and maintained. Many organizations overlook basic security practices, leaving their SSH setups vulnerable to brute force attacks, unauthorized logins, and other exploits. By following best practices and implementing advanced security measures, you can significantly reduce risks and enhance the safety of your infrastructure.
This article will guide you through the intricacies of securing remote SSH access, covering everything from fundamental configurations to cutting-edge techniques. Whether you’re a beginner learning the ropes or an experienced professional looking to refine your skills, this guide will provide actionable insights to protect your SSH connections. Let’s dive in and explore the world of SSH security.
Read also:Anderson Livestock Auction Utah Your Gateway To Topquality Livestock Trading
Table of Contents
- 1. Why Is Securing Remote SSH Access Important?
- 2. What Are the Common SSH Security Threats?
- 3. How Can You Strengthen SSH Authentication?
- 4. Best Practices for Securing Remote SSH Access
- 5. Is SSH Encryption Enough to Protect Your Data?
- 6. Securing Remote SSH Access: Role of Firewall Configuration
- 7. How to Monitor and Audit SSH Connections
- 8. Frequently Asked Questions About SSH Security
- 9. Conclusion: Taking Control of Your SSH Security
Why Is Securing Remote SSH Access Important?
In the realm of network security, SSH plays a pivotal role in enabling secure communication between devices. Securing remote SSH access isn’t merely about safeguarding your servers; it’s about protecting sensitive information, maintaining operational integrity, and ensuring compliance with industry standards. Without robust SSH security, your organization risks exposure to a wide array of cyber threats, from brute force attacks to man-in-the-middle (MITM) exploits.
SSH is often considered a secure protocol because it encrypts data during transmission. However, this encryption alone isn’t sufficient if proper security measures aren’t implemented. For instance, using default settings, weak passwords, or outdated software can render even the most secure SSH connections vulnerable. The importance of securing remote SSH access cannot be overstated, especially in environments where sensitive data is transmitted regularly.
Consider the following scenarios: A hacker gains unauthorized access to your server through an unsecured SSH connection, stealing customer data and intellectual property. Or imagine a ransomware attack encrypting critical files after breaching your system via SSH. These examples highlight why securing SSH access is paramount. By adopting proactive security strategies, you can mitigate these risks and ensure the resilience of your digital infrastructure.
What Are the Common SSH Security Threats?
While SSH is inherently designed to be secure, several vulnerabilities and threats can compromise its integrity. Understanding these threats is the first step toward effective mitigation. Below are some of the most prevalent SSH security threats:
- Brute Force Attacks: Hackers use automated tools to repeatedly guess passwords until they gain access.
- Man-in-the-Middle Attacks: Attackers intercept communications between two parties, impersonating each side to steal sensitive information.
- Weak Passwords: Simple or predictable passwords make it easier for attackers to breach SSH connections.
- Outdated Software: Failing to update SSH clients and servers leaves them exposed to known vulnerabilities.
- Unencrypted Data Transmission: Improper configurations can result in unencrypted data being transmitted, making it susceptible to interception.
Each of these threats poses significant risks to your system’s security. By identifying potential vulnerabilities, you can implement targeted solutions to enhance your SSH setup’s resilience against malicious activities.
How Can You Strengthen SSH Authentication?
Authentication lies at the heart of securing remote SSH access. By reinforcing your authentication mechanisms, you can significantly bolster the security of your SSH connections. Here are several strategies to strengthen SSH authentication:
Read also:Unlock The Potential Of Your Sone 436 Plot A Comprehensive Guide To Smart Investments
1. Disable Password Authentication
One of the simplest yet most effective ways to enhance SSH security is to disable password authentication entirely. Instead, rely on key-based authentication, which uses cryptographic keys to verify identity. This method eliminates the risk of weak or compromised passwords.
2. Use Strong SSH Keys
When employing key-based authentication, ensure that your SSH keys are strong and unique. Longer keys (e.g., 4096-bit RSA or ECC keys) offer greater resistance to brute force attacks. Additionally, protect your private keys with passphrases for an added layer of security.
3. Implement Multi-Factor Authentication (MFA)
MFA adds another layer of protection by requiring users to provide multiple forms of identification before gaining access. Combining key-based authentication with MFA ensures that even if a key is compromised, unauthorized access remains improbable.
Best Practices for Securing Remote SSH Access
Beyond authentication, numerous best practices contribute to securing remote SSH access. These practices address various aspects of SSH security, from configuration to monitoring. Below are some key recommendations:
Change Default Settings
Default SSH settings often include the standard port (22) and root login permissions. Changing these defaults can deter automated attacks:
- Change the SSH Port: Move SSH from port 22 to a non-standard port to reduce visibility to attackers.
- Disable Root Login: Restrict direct root access to prevent unauthorized users from gaining administrative privileges.
Regularly Update Software
Keeping your SSH client and server software up to date is crucial. Software updates often include patches for newly discovered vulnerabilities, ensuring your SSH setup remains secure against emerging threats.
Limit User Access
Restrict SSH access to only those users who genuinely need it. Use group policies or user lists to control who can connect to your servers, reducing the attack surface.
Is SSH Encryption Enough to Protect Your Data?
SSH encryption is undoubtedly a powerful tool for securing data transmission. However, relying solely on encryption can leave gaps in your security framework. While encryption protects data in transit, it doesn’t address other critical areas such as authentication, access control, and monitoring.
To ensure comprehensive protection, combine SSH encryption with complementary security measures. For example, implement strict access controls, regularly audit logs, and employ intrusion detection systems. By adopting a multi-layered approach, you can fortify your SSH security and safeguard your data against a broader range of threats.
Securing Remote SSH Access: Role of Firewall Configuration
Firewalls act as a barrier between your internal network and external threats, playing a crucial role in securing remote SSH access. Proper firewall configuration can restrict unauthorized access and filter malicious traffic. Here’s how to leverage firewalls for enhanced SSH security:
Allow Specific IP Addresses
Configure your firewall to allow SSH connections only from trusted IP addresses. This reduces the likelihood of unauthorized access attempts and minimizes exposure to brute force attacks.
Set Time Restrictions
Limit the times during which SSH connections are permitted. For instance, if your team works within specific hours, restrict SSH access outside those periods to minimize risks.
How to Monitor and Audit SSH Connections
Monitoring and auditing SSH connections are essential for detecting and responding to potential security incidents. Regular monitoring helps identify suspicious activities, while audits ensure compliance with security policies. Below are strategies for effective monitoring and auditing:
Enable Logging
Activate detailed logging for SSH connections. Logs provide valuable insights into who accessed your systems, when, and from where. Analyze logs regularly to identify patterns or anomalies that may indicate unauthorized access attempts.
Implement Intrusion Detection Systems (IDS)
Deploy IDS to monitor network traffic and detect potential intrusions. These systems can alert you to suspicious activities and help prevent breaches before they escalate.
Frequently Asked Questions About SSH Security
1. Can SSH Be Hacked?
Yes, SSH can be hacked if proper security measures aren’t implemented. Common vulnerabilities include weak passwords, outdated software, and misconfigurations. To minimize risks, adopt best practices such as key-based authentication, regular updates, and firewall configuration.
2. Is SSH Secure Without a Password?
SSH can be secure without a password if key-based authentication is properly configured. Using strong SSH keys and protecting them with passphrases enhances security and reduces the risk of unauthorized access.
3. Should I Use SSH on Public Wi-Fi?
Using SSH on public Wi-Fi is generally safe due to its encryption capabilities. However, always ensure your SSH client and server are up to date and avoid connecting to untrusted networks whenever possible.
Conclusion: Taking Control of Your SSH Security
Securing remote SSH access is a multifaceted process that requires attention to detail and adherence to best practices. From strengthening authentication mechanisms to implementing robust monitoring strategies, each step contributes to building a secure SSH environment. By following the guidelines outlined in this article, you can significantly enhance the security of your SSH connections and protect your systems from potential threats.
Remember, cybersecurity is an ongoing effort. Stay informed about emerging threats and continuously refine your security measures to stay one step ahead of attackers. With dedication and diligence, you can master securing remote SSH access and ensure the safety of your digital infrastructure.