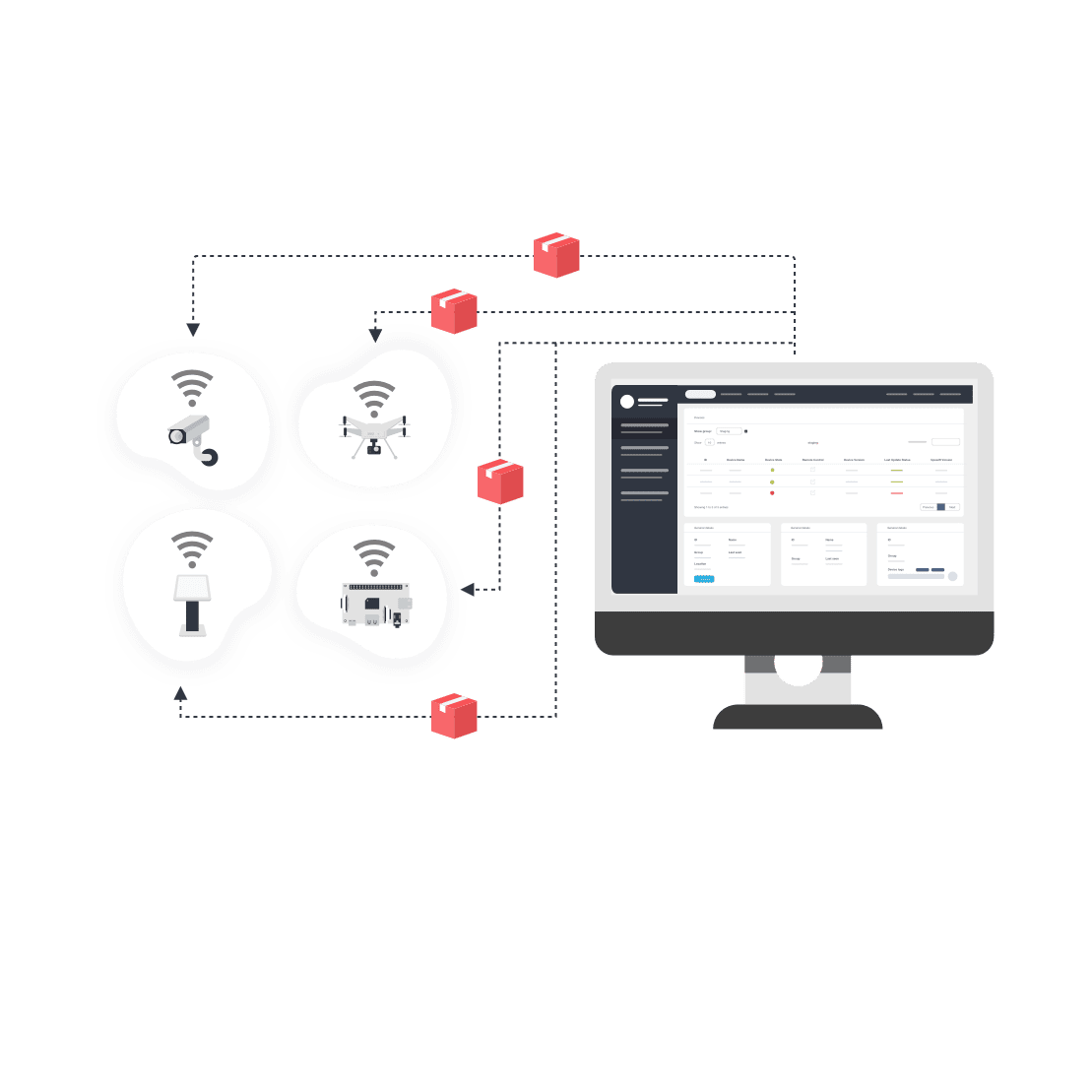
In today's interconnected world, managing IoT devices behind a firewall using Ubuntu has become a critical skill for IT professionals and hobbyists alike. As the Internet of Things continues to expand, securing these devices against cyber threats is more important than ever. An Ubuntu-based solution offers robust tools and flexibility, allowing users to maintain control over their IoT ecosystem while ensuring privacy and security. This article dives deep into the "manage IoT device behind firewall Ubuntu example," providing practical insights, step-by-step instructions, and expert tips to help you master this essential process.
Managing IoT devices behind a firewall is not just about protecting your network; it's about creating a resilient infrastructure that can adapt to evolving security challenges. Whether you're setting up smart home devices, industrial sensors, or healthcare equipment, Ubuntu provides the perfect platform for configuring firewalls, managing access, and monitoring activity. This guide will walk you through everything from basic setup to advanced configurations, ensuring your IoT devices remain secure and operational.
By the end of this article, you'll have a comprehensive understanding of how to manage IoT devices behind a firewall using Ubuntu. You'll learn about the best practices, common pitfalls, and troubleshooting techniques that will empower you to build a secure and efficient IoT environment. Let's get started!
Read also:Unveiling The Hype Exploring The World Of Movierulz Kannada Movie 2025
Table of Contents
- 1. What Is the Importance of Managing IoT Devices Behind a Firewall?
- 2. How Can You Set Up an Ubuntu-Based Firewall for IoT Devices?
- 3. Why Choose Ubuntu for Managing IoT Devices?
- 4. Managing IoT Devices Behind Firewall: Step-by-Step Guide
- 5. Is It Necessary to Use SSH for Secure Connections?
- 6. Advanced Techniques: Automating IoT Device Management
- 7. Troubleshooting Common Issues in IoT Device Management
- 8. Manage IoT Device Behind Firewall Ubuntu Example: Practical Case Study
What Is the Importance of Managing IoT Devices Behind a Firewall?
In an era where billions of IoT devices are deployed globally, securing these devices has become paramount. A firewall acts as the first line of defense against unauthorized access, protecting your IoT devices from potential cyberattacks. By managing IoT devices behind a firewall, you ensure that only trusted traffic enters or exits your network, reducing the risk of data breaches and malicious activity.
IoT devices often lack robust built-in security features, making them vulnerable to attacks. Placing them behind a firewall adds an additional layer of protection, allowing you to control who and what can interact with these devices. Additionally, firewalls enable you to monitor network activity, detect suspicious behavior, and respond quickly to threats. This proactive approach is crucial for maintaining the integrity and reliability of your IoT ecosystem.
Furthermore, managing IoT devices behind a firewall helps comply with industry regulations and standards. Many industries require organizations to implement stringent security measures to protect sensitive data. By adhering to best practices in firewall management, you can demonstrate your commitment to data protection and enhance your organization's reputation.
Why Should You Care About IoT Security?
IoT security is not just a technical issue; it's a business imperative. A single security breach can result in financial losses, reputational damage, and legal consequences. For example, if a smart thermostat in a commercial building is compromised, it could lead to unauthorized access to the entire HVAC system, causing operational disruptions. Similarly, a hacked medical device could endanger patient safety, leading to severe ethical and legal ramifications.
To mitigate these risks, it's essential to adopt a comprehensive security strategy that includes managing IoT devices behind a firewall. This approach ensures that your devices remain protected, your data remains confidential, and your operations run smoothly.
What Are the Benefits of Using a Firewall for IoT Devices?
- Enhanced security through controlled access
- Improved network performance by blocking unnecessary traffic
- Centralized management for easier monitoring and maintenance
- Compliance with regulatory requirements
- Reduced risk of cyberattacks and data breaches
How Can You Set Up an Ubuntu-Based Firewall for IoT Devices?
Ubuntu is a powerful Linux distribution that offers a wide range of tools and utilities for setting up a firewall. One of the most popular firewall solutions for Ubuntu is UFW (Uncomplicated Firewall), which provides a user-friendly interface for managing network traffic. By leveraging UFW, you can easily configure rules to control inbound and outbound connections, ensuring your IoT devices remain secure.
Read also:Unveiling The World Of Wasmo Telegram A Comprehensive Guide
To set up an Ubuntu-based firewall for IoT devices, follow these steps:
- Install Ubuntu on your server or desktop machine.
- Update your system using the command
sudo apt update && sudo apt upgrade. - Install UFW by running
sudo apt install ufw. - Enable the firewall with
sudo ufw enable. - Configure rules to allow or deny specific types of traffic.
For example, if you want to allow SSH access from a specific IP address, you can use the command sudo ufw allow from [IP address] to any port 22. Similarly, you can deny access to certain ports or IP ranges to enhance security.
What Are the Key Features of UFW?
UFW simplifies the process of configuring a firewall by providing intuitive commands and options. Some of its key features include:
- Easy-to-use syntax for adding and removing rules
- Support for IPv4 and IPv6
- Logging capabilities for tracking network activity
- Integration with other Ubuntu services and tools
By mastering UFW, you can effectively manage your IoT devices behind a firewall, ensuring they remain protected from potential threats.
Why Choose Ubuntu for Managing IoT Devices?
Ubuntu stands out as one of the best platforms for managing IoT devices due to its stability, security, and flexibility. As a leading Linux distribution, Ubuntu offers a wide range of tools and libraries specifically designed for IoT applications. Its strong community support and regular updates ensure that you always have access to the latest features and security patches.
One of the key advantages of using Ubuntu for IoT device management is its compatibility with various hardware platforms. Whether you're working with Raspberry Pi, BeagleBone, or other single-board computers, Ubuntu provides a seamless experience for configuring and controlling IoT devices. Additionally, Ubuntu's extensive package repository allows you to install and integrate third-party tools and applications effortlessly.
Another reason to choose Ubuntu is its focus on security. The distribution includes built-in tools for managing firewalls, encryption, and authentication, making it an ideal choice for securing IoT devices. By leveraging Ubuntu's security features, you can create a robust and reliable environment for your IoT ecosystem.
What Makes Ubuntu Ideal for IoT Applications?
Ubuntu excels in several areas that make it perfect for IoT applications:
- Lightweight and efficient, suitable for resource-constrained devices
- Wide range of supported hardware and software
- Regular updates and long-term support
- Strong community and enterprise support
These advantages position Ubuntu as the go-to platform for managing IoT devices behind a firewall.
Managing IoT Devices Behind Firewall: Step-by-Step Guide
Now that you understand the importance of managing IoT devices behind a firewall and the benefits of using Ubuntu, let's dive into a step-by-step guide for implementing this solution. This section will walk you through the entire process, from initial setup to advanced configurations.
Step 1: Install Ubuntu and Configure the Firewall
Begin by installing Ubuntu on your server or desktop machine. Once installed, update your system and install UFW as described earlier. Configure the firewall to allow only necessary traffic, such as SSH and HTTP, while blocking all other connections.
Step 2: Connect Your IoT Devices
Connect your IoT devices to the network and ensure they are accessible from the Ubuntu machine. You may need to configure static IP addresses or DNS settings to facilitate communication.
Step 3: Secure Communication with SSH
Use SSH to establish secure connections between your IoT devices and the Ubuntu machine. This ensures that all communication is encrypted and protected from eavesdropping.
Step 4: Monitor and Maintain Your IoT Ecosystem
Regularly monitor your IoT devices for signs of unusual activity and apply security patches as needed. Keep your firewall rules up to date and review your network configuration periodically to ensure optimal performance.
Is It Necessary to Use SSH for Secure Connections?
Yes, using SSH is essential for securing communication between your IoT devices and the Ubuntu machine. SSH provides end-to-end encryption, ensuring that your data remains confidential and tamper-proof. Without SSH, your devices could be vulnerable to man-in-the-middle attacks and other security threats.
How Can You Configure SSH for IoT Devices?
Configuring SSH for IoT devices involves several steps:
- Install an SSH server on your IoT devices if they don't already have one.
- Generate SSH keys on your Ubuntu machine using the command
ssh-keygen. - Copy the public key to your IoT devices using
ssh-copy-id. - Test the connection by logging in to your IoT devices via SSH.
By following these steps, you can establish secure connections between your IoT devices and the Ubuntu machine, enhancing the overall security of your network.
Advanced Techniques: Automating IoT Device Management
As your IoT ecosystem grows, managing devices manually can become time-consuming and error-prone. To streamline this process, consider automating various aspects of IoT device management. Automation not only saves time but also reduces the risk of human error, ensuring your devices remain secure and operational.
One popular tool for automating IoT device management is Ansible. Ansible allows you to define playbooks that specify the desired state of your IoT devices and apply those configurations automatically. By leveraging Ansible, you can manage multiple devices simultaneously, making it easier to scale your IoT infrastructure.
Another technique is to use IoT platforms that offer built-in automation capabilities. These platforms often include features such as device discovery, configuration management, and monitoring, simplifying the process of managing IoT devices behind a firewall.
What Are the Benefits of Automating IoT Device Management?
Automating IoT device management offers several advantages:
- Improved efficiency and reduced workload
- Consistent configuration across all devices
- Enhanced security through automated updates and patches
- Real-time monitoring and alerts for potential issues
By embracing automation, you can take your IoT device management to the next level, ensuring your network remains secure and optimized.
Troubleshooting Common Issues in IoT Device Management
Despite your best efforts, issues may arise when managing IoT devices behind a firewall. Common problems include connectivity issues, firewall misconfigurations, and device malfunctions. In this section, we'll explore some of these challenges and provide solutions to help you overcome them.
Issue 1: Connectivity Problems
If your IoT devices are unable to connect to the network, check the following:
- Ensure that the devices are properly connected to the network and have valid IP addresses.
- Verify that the firewall rules allow necessary traffic, such as SSH and HTTP.
- Test the connection using tools like
pingandtraceroute.
Issue 2: Firewall Misconfigurations
Misconfigured firewall rules can block legitimate traffic or allow unauthorized access. To resolve this:
- Review your firewall rules and ensure they align with your security requirements.
- Use logging to identify and analyze suspicious activity.
- Test your rules by simulating various scenarios and observing the results.
Issue 3: Device Malfunctions
If an IoT device stops functioning correctly, try the following:
- Restart the device and check for any error messages.
- Update the device firmware to the latest version.
- Consult the device documentation for troubleshooting tips.
How Can You Prevent IoT Device Management Issues?
To minimize the likelihood of encountering issues, adopt preventive measures such as:
- Regularly updating your devices and software
- Monitoring network activity for signs of unusual behavior
- Performing routine maintenance and backups
By staying proactive, you can ensure your IoT devices remain secure and operational.
Manage IoT Device Behind Firewall Ubuntu Example: Practical Case Study
To illustrate the concepts discussed in this article, let's examine