In today's interconnected world, managing remote IoT devices through SSH has become a cornerstone of modern digital infrastructure. RemoteIoT SSH की व्यवस्थापन allows organizations to securely control and monitor their IoT ecosystems, ensuring seamless operations from anywhere in the world. As businesses increasingly rely on IoT technologies, understanding how to effectively manage these systems is crucial for maintaining efficiency, security, and reliability. From small startups to large enterprises, the ability to remotely access and configure IoT devices via SSH is transforming the way we interact with technology.
However, with great power comes great responsibility. Managing remote IoT devices through SSH requires a deep understanding of both cybersecurity principles and technical best practices. This article will serve as your ultimate guide to mastering RemoteIoT SSH management, covering everything from basic configurations to advanced troubleshooting techniques. Whether you're a beginner looking to understand the fundamentals or an experienced professional seeking to refine your skills, this comprehensive resource has something for everyone.
As we delve deeper into the intricacies of RemoteIoT SSH की व्यवस्थापन, you'll discover practical tips, real-world examples, and actionable strategies to enhance your capabilities. By the end of this article, you'll have a solid foundation to confidently manage your IoT infrastructure while minimizing risks and maximizing performance. Let's embark on this journey together and unlock the full potential of remote IoT management through SSH.
Read also:Discover The Ultimate Entertainment Hub Hd Hub 4 U Com For Seamless Hd Streaming
Table of Contents
- 1. What is RemoteIoT SSH Management?
- 2. Why Should You Care About RemoteIoT SSH की व्यवस्थापन?
- 3. How Does RemoteIoT SSH Management Work?
- 4. Can RemoteIoT SSH Management Enhance Security?
- 5. Key Benefits of Implementing RemoteIoT SSH की व्यवस्थापन
- 6. Best Practices for RemoteIoT SSH Management
- 7. What Are the Common Challenges in RemoteIoT SSH Management?
- 8. Future Trends in RemoteIoT SSH Management
What is RemoteIoT SSH Management?
RemoteIoT SSH management refers to the practice of securely accessing, configuring, and maintaining Internet of Things (IoT) devices through Secure Shell (SSH) protocols. SSH is a cryptographic network protocol that facilitates secure communication between devices over an unsecured network. In the context of IoT, this means organizations can remotely manage their connected devices without compromising data integrity or system security.
At its core, RemoteIoT SSH की व्यवस्थापन enables administrators to perform essential tasks such as firmware updates, configuration changes, and diagnostic checks from a centralized location. This capability is particularly valuable for enterprises with distributed IoT infrastructures spanning multiple geographic locations. By leveraging SSH, organizations can reduce the need for physical site visits, streamline operations, and lower costs associated with manual interventions.
Moreover, SSH provides robust authentication mechanisms and encryption protocols to safeguard sensitive information during transmission. This ensures that even if unauthorized parties intercept communication channels, they won't be able to decipher the data being exchanged. As a result, RemoteIoT SSH management has become an indispensable tool for businesses seeking to maintain control over their IoT ecosystems while adhering to stringent security standards.
Why Should You Care About RemoteIoT SSH की व्यवस्थापन?
In an era where cybersecurity threats are constantly evolving, ensuring the safety and integrity of IoT devices has never been more critical. RemoteIoT SSH की व्यवस्थापन offers a powerful solution to address these challenges by providing a secure and reliable method for managing connected devices. Here are some compelling reasons why you should prioritize implementing this technology:
- Enhanced Security: SSH employs strong encryption algorithms and authentication protocols to protect against unauthorized access and data breaches.
- Improved Efficiency: By enabling remote management capabilities, organizations can resolve issues faster and perform routine maintenance tasks without requiring on-site personnel.
- Cost Savings: Reducing the need for physical interventions leads to significant cost reductions in terms of travel expenses, labor costs, and downtime.
- Scalability: As your IoT infrastructure grows, RemoteIoT SSH management allows you to maintain consistent control over all devices regardless of their location or number.
In summary, adopting RemoteIoT SSH की व्यवस्थापन not only strengthens your organization's security posture but also enhances operational efficiency and reduces expenses. These benefits make it an attractive option for businesses across various industries looking to leverage IoT technologies effectively.
How Does RemoteIoT SSH Management Work?
To understand how RemoteIoT SSH management operates, let's break down the process into its fundamental components:
Read also:Kev On Stage Net Worth The Untold Story Of A Digital Mogul
- Connection Establishment: The administrator initiates an SSH connection with the target IoT device using a unique identifier such as an IP address or hostname.
- Authentication: Before granting access, the system verifies the user's identity through methods like password-based authentication or public key cryptography.
- Secure Communication: Once authenticated, the session begins, and all subsequent interactions between the client and server are encrypted to prevent eavesdropping and tampering.
- Command Execution: Administrators can execute commands remotely to perform actions such as updating software, modifying configurations, or retrieving logs.
- Session Termination: Upon completion of the desired tasks, the connection is securely closed, ensuring no residual vulnerabilities remain.
This structured approach ensures that every aspect of the management process adheres to strict security guidelines, minimizing risks associated with unauthorized access or malicious activities.
Can RemoteIoT SSH Management Enhance Security?
Absolutely! One of the primary advantages of RemoteIoT SSH management lies in its ability to significantly bolster security measures for IoT devices. By utilizing advanced encryption techniques and secure authentication protocols, SSH creates a fortified barrier against potential threats. Furthermore, its support for features like two-factor authentication and role-based access control adds another layer of protection, making it even harder for attackers to compromise systems.
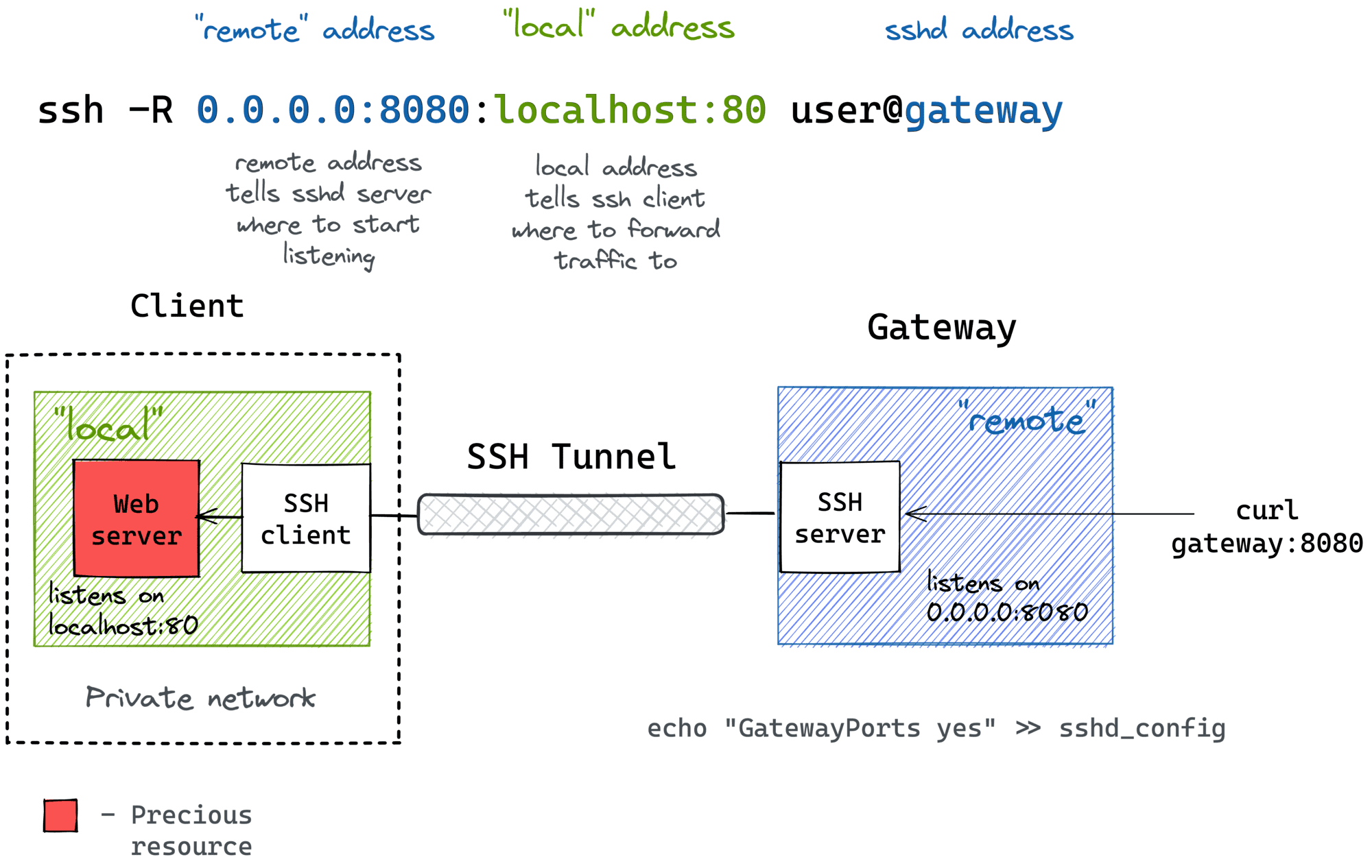
In addition to safeguarding individual devices, RemoteIoT SSH management also contributes to strengthening overall network security. For instance, by implementing SSH tunneling, sensitive communications can be routed through secure channels, shielding them from prying eyes. Similarly, regular audits and monitoring of SSH activity help identify suspicious patterns early, allowing for swift action to mitigate any emerging risks.
Key Benefits of Implementing RemoteIoT SSH की व्यवस्थापन
Implementing RemoteIoT SSH की व्यवस्थापन offers numerous advantages that extend beyond just enhancing security. Let's explore some of the most significant benefits:
- Centralized Control: Administrators can manage multiple IoT devices simultaneously from a single interface, simplifying oversight and coordination.
- Real-Time Monitoring: Access to live performance metrics and diagnostic information enables proactive identification and resolution of issues before they escalate.
- Automated Processes: Scripting capabilities within SSH allow for the automation of repetitive tasks, freeing up valuable time for more critical responsibilities.
- Compliance Adherence: By maintaining detailed logs of all SSH sessions, organizations can demonstrate compliance with industry regulations and internal policies.
These benefits collectively contribute to a more streamlined and secure IoT ecosystem, empowering businesses to achieve their objectives more effectively.
Best Practices for RemoteIoT SSH Management
To maximize the effectiveness of RemoteIoT SSH management, it's essential to follow established best practices. Here are some recommendations:
- Use Strong Passwords: Ensure that all SSH accounts have complex passwords that are difficult to guess or crack.
- Enable Two-Factor Authentication: Add an extra layer of security by requiring users to provide two forms of identification before granting access.
- Regularly Update Software: Keep both the SSH client and server software up-to-date to patch vulnerabilities and incorporate new features.
- Limit User Privileges: Assign appropriate permissions based on job roles to minimize the risk of accidental or intentional misuse.
Adhering to these guidelines will help you create a robust RemoteIoT SSH management framework that supports your organization's goals while mitigating potential risks.
What Are the Common Challenges in RemoteIoT SSH Management?
Despite its many advantages, RemoteIoT SSH management does present certain challenges that must be addressed:
- Complex Configuration: Setting up and maintaining SSH environments can be intricate, requiring specialized knowledge and expertise.
- Network Latency: Geographically dispersed IoT devices may experience delays in communication due to network conditions, impacting responsiveness.
- Resource Constraints: Limited computational power on some IoT devices might hinder the efficient execution of SSH processes.
By anticipating these obstacles and developing strategies to overcome them, organizations can optimize their RemoteIoT SSH management efforts.
Future Trends in RemoteIoT SSH Management
As technology continues to advance, several emerging trends are likely to shape the future of RemoteIoT SSH management:
- Artificial Intelligence Integration: AI-driven analytics will enhance predictive maintenance capabilities, enabling smarter decision-making.
- Quantum Cryptography: Next-generation encryption methods will provide unprecedented levels of security, safeguarding against future threats.
- Edge Computing Adoption: Processing data closer to the source will reduce latency and improve overall performance of IoT systems.
Embracing these innovations will position organizations at the forefront of IoT evolution, ensuring they remain competitive in an increasingly digital landscape.
FAQs
1. How secure is RemoteIoT SSH management?
RemoteIoT SSH management is highly secure when implemented correctly. Its use of encryption, authentication protocols, and access controls makes it a reliable method for managing IoT devices remotely.
2. Can I automate tasks using RemoteIoT SSH की व्यवस्थापन?
Yes, scripting within SSH allows for the automation of repetitive tasks, saving time and reducing errors associated with manual interventions.
3. What are some common mistakes to avoid in RemoteIoT SSH management?
Using weak passwords, neglecting software updates, and granting excessive privileges are among the most common mistakes that should be avoided to maintain a secure environment.
Conclusion
Mastering RemoteIoT SSH की व्यवस्थापन is essential for anyone involved in managing IoT infrastructures. By understanding its principles, benefits, and challenges, you can harness its full potential to drive your organization's success in today's digital age. Stay informed about emerging trends and continuously refine your practices to remain ahead of the curve in this rapidly evolving field.